Mirador Managed Defense MDR
Confidently secure technologies you already own
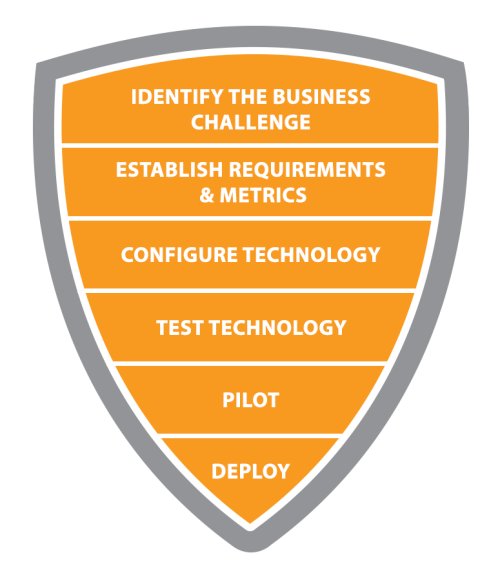
Mirador Managed Detection and Response (MDR) maximizes the value from all deployed Microsoft solutions, including Microsoft Defender for Endpoint (MDE), Microsoft 365 Defender, Microsoft Defender for Cloud, Microsoft Sentinel and services provided in Mirador Managed Defense MDR, Mirador Managed Defense SIEM.
Get Started Today

Why Use CrucialLogics?
ENDPOINT MONITORING
Attackers target vulnerable endpoints, so trust deployed Microsoft Defender Solutions and Microsoft Sentinel to collect and aggregate data, analyze it to detect potential threats, and alert the Mirador Managed Defense Microsoft Defender MDR team in real-time.
ACTIVE ENDPOINT PROTECTION
When Microsoft Defender for Endpoint detects a threat, it can automatically react and delete malware, interrupt attacks, or isolate the system from the endpoint to prevent the attack from spreading.
ANOMALY DETECTION AND ARTIFICIAL INTELLIGENCE
AI recognizes and stops attacks faster by detecting threats and anomalies through data analysis that extracts patterns and trends pointing to potential intrusions and other issues on the system.
ENDPOINT LOG MANAGEMENT
Endpoints generate many log files that are often ignored. Automatic log management makes this data readily available to its own data analytics systems and human analysts while providing investigators access to the compiled results and linked processes.
INVESTIGATION & RESPONSE
24×7 monitoring and incident triage, advanced hunting, live response, and deep analysis on malware file detonations.
GET SECURE TODAY
Testimonials



How We Work
We remove the barriers that make cybersecurity complex. We deeply understand attacker behaviour and how to secure against them.