Windows 365
Solve device management and data security challenges.
Windows 365 cloud PC is an innovative cloud-based service from Microsoft that allows businesses to create and manage their own virtual machines or Cloud PCs. This powerful platform solves device management and data security challenges by providing a dedicated Windows device for each user. Enjoy the productivity and collaboration benefits of the Microsoft 365 suite, while also benefiting from enhanced security features.
Get Started Today

Why Windows 365?
EASE OF USE
Get cloud-based computing, storage, and collaboration options that are secure, reliable, and efficient, all while keeping costs down and providing easy access to the applications and services they need.
FAST IMPLEMENTATION
Quickly set up virtual machines (Cloud PCs) for users, ensuring that each individual user has a dedicated Windows device tailored to their needs.
EASILY SCALE UP OR DOWN
Easily scale up or down as needed without investing in additional hardware or software licenses.
SECURE
Security is enhanced through features such as automatic security updates and advanced threat protection, which reduces the risk of malware infections on endpoints.
INTEGRATIONS
Integrate with Microsoft Endpoint Manager for more management options for their Cloud PCs. Easily configure settings remotely and centrally manage user access across multiple devices without needing extra on-site IT staff members.
REMOTE ACCESS
Allow remote employees to access their assigned Cloud PC from anywhere using any device, meaning they can work on the same files even if they’re not at the office location itself.
COLLABORATE EASILY
Stay connected with co-workers regardless of location with unified communication tools like chat messaging and video conferencing capabilities.
Get Secure Cloud Computing Today
Testimonials



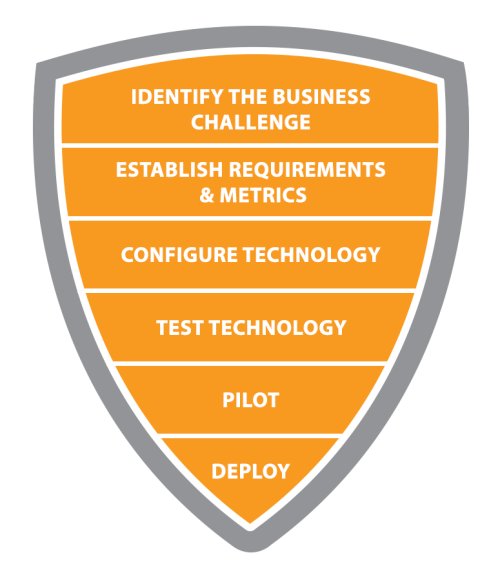
How We Work
We remove the barriers that make cybersecurity complex. We deeply understand attacker behavior and how to secure against them.