Outlook vs Gmail: How do They Compare for Personal & Business Usage [2025 Guide]

Outlook vs. Gmail: A 2024 comparison to help you choose the right email for personal or business use. Discover which email platform is best for you
Data Loss Prevention Protect Your Data with a Risk Plan

Protecting your data means having a plan and working to prevent and mitigate damage. Understand what can go wrong so that if it ever happens, you know exactly what to do to get back up and running.
How to Prevent Cyber Attacks: Keeping Your Business Safe

With hackers finding new and creative ways to exploit vulnerabilities in both corporate and government systems, the cost of these breaches can be staggering.
Features & Benefits of Microsoft 365 for Businesses
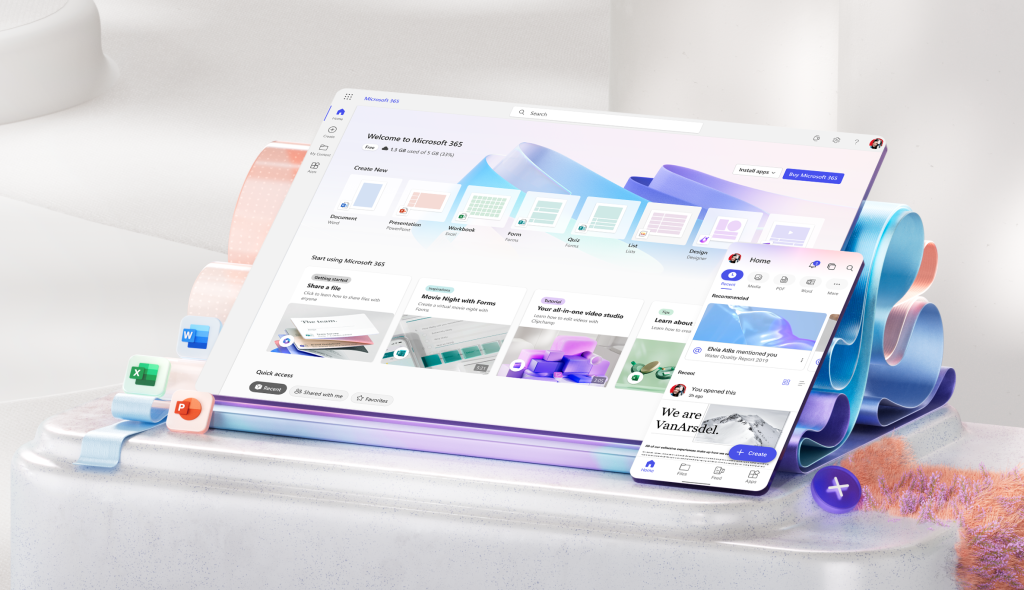
Explore the 12 ways Microsoft 365 can revolutionize your business, from boosting productivity to gaining powerful data insights.
Data Security Issues: How to Lose Your Data in 10 Days

Learn how to avoid data loss in just 10 days with these 10 common IT security missteps. From phishing to poor password practices, cruciallogics has the solutions to keep your data safe.
Network Eavesdropping: Experts Uncover New Wi-Fi Vulnerability

Discover a new Wi-Fi vulnerability exposing users to eavesdropping attacks, affecting major operating systems. Learn about the SSID Confusion attack and essential mitigation strategies.
Industry Alignment with V3 Cybersecurity Minerva

CrucialLogics is excited to offer our clients Minerva™ technology to streamline the migration process and add value in taking our clients to the cloud.
4 Cybersecurity Solutions Everyone Is Talking About

Investing in solutions such as cloud security, IAM, endpoint protection, and automation, can protect companies from the risks of cybercrime. Read how.
A Guide to Cloud Security Monitoring & Benefits (+best practices)

Cloud security monitoring is the process of monitoring and analyzing the security of cloud infrastructure, networks and applications. Learn more!
Cloud Migration Security Risks (+ Checklist & Strategy)

Securely migrate to the cloud with Cloud Migration Security. Learn how to navigate challenges with an applicable strategy during transfer.

